Understanding UUIDs: Types and Applications
Explore the different versions of Universally Unique Identifiers (UUIDs) and their specific uses.
Category: Data Security | Published: May 1, 2024 | Author:  Renato Cassino
Renato Cassino
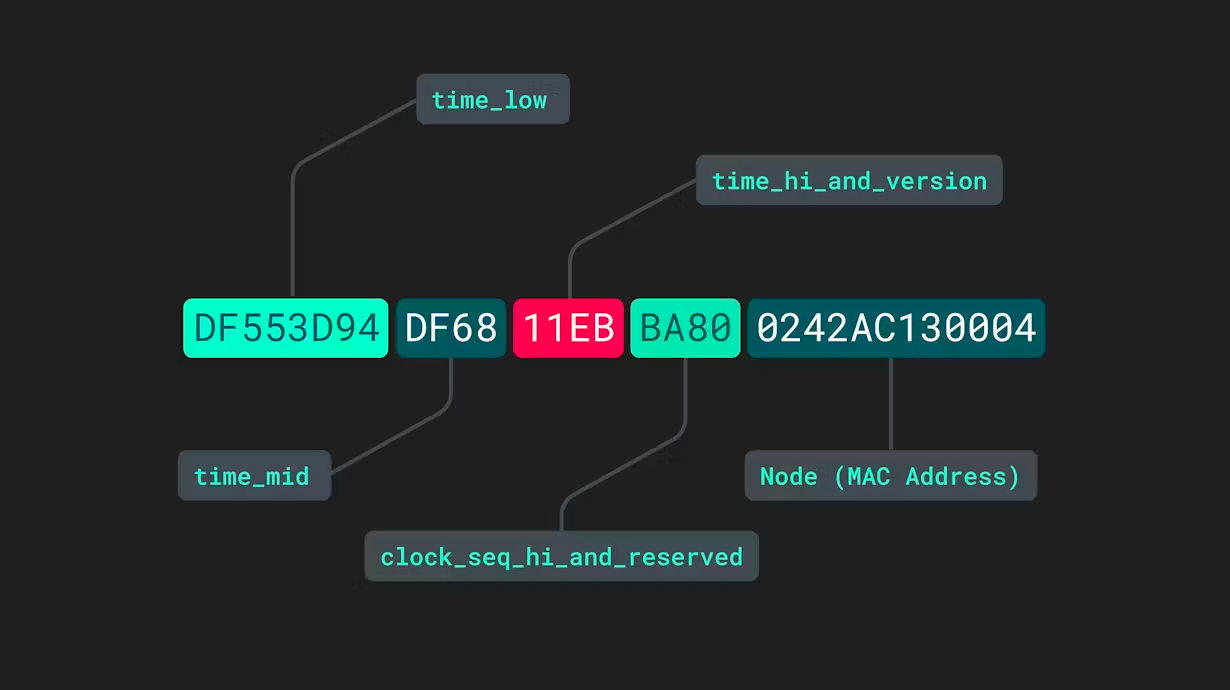
Universally Unique Identifiers (UUIDs) are 128-bit numbers used to uniquely identify information in computer systems. While the concept might seem simple, the different versions of UUIDs cater to various requirements of uniqueness and randomness, depending on their application context. This article delves into three of the most commonly used versions: UUID v1, UUID v4, and UUID v5.
UUID Version 1 (Time-Based)
UUID v1 is generated from the timestamp of the moment of generation, the clock sequence, and the unique MAC address of the computer on which it was generated. This version guarantees uniqueness by combining the precise timestamp with specific system hardware details, making it nearly impossible for two identical UUIDs to be created:
- Pros: Ensures a historical sequence of IDs.
- Cons: Potential privacy concerns since it incorporates the MAC address of the generating computer.
UUID Version 4 (Random)
UUID v4 relies purely on random numbers. A UUID v4 is generated by randomly choosing each bit of the UUID, providing a simple and quick solution for generating identifiers with a minimal chance of collision:
- Pros: Easy to generate and no privacy issues compared to v1.
- Cons: No guarantee of uniqueness, although the probability of duplicates is extremely low.
UUID Version 5 (Name-Based and SHA-1)
UUID v5 uses a name-based method where a namespace identifier and a specific name are hashed using SHA-1. The use of a deterministic hash function means that the same name and namespace will always produce the same UUID v5:
- Pros: Useful when you need consistent UUIDs for the same input values.
- Cons: Since it is deterministic, UUID v5 is not suitable for all applications, particularly those needing high levels of randomness.
Conclusion
UUIDs offer a versatile range of options for generating unique identifiers across various applications. Whether you need time-based sequencing, pure randomness, or deterministic IDs, there is a UUID version to meet your requirements. They play a crucial role in systems where the uniqueness of identifiers is critical, such as in databases, networking, and for maintaining data integrity across distributed systems.
Other posts
Understanding Base64: Encoding and Decoding Explained
Learn how Base64 encoding works and how it can be used to encode and decode data.

The Importance of Strong Passwords: Safeguarding Your Digital Life
Learn why strong passwords are crucial and how they protect your online accounts.
Understanding Computer Colors: RGB and Hexadecimal Explained
Dive into how computers display colors using the RGB color model and hexadecimal values.

Understanding MD5: The Hashing Algorithm Explained
Explore how the MD5 algorithm works and its applications in digital security.