Understanding MD5: The Hashing Algorithm Explained
Explore how the MD5 algorithm works and its applications in digital security.
Category: Cybersecurity | Published: May 12, 2024 | Author:  Renato Cassino
Renato Cassino

MD5, or Message-Digest Algorithm 5, is a widely used cryptographic hash function that produces a 128-bit (16-byte) hash value. Typically used to ensure data integrity, MD5 has been utilized in a variety of security applications and is also commonly employed to verify data consistency.
How Does MD5 Work?
MD5 processes data in blocks, each of which influences the hash that is produced. Essentially, MD5 takes an input (or 'message') and returns a fixed-size, 128-bit hash value, typically rendered as a 32-character hexadecimal number. This hash is designed to be unique to the original input, meaning even a small change in the input will produce a significantly different output hash.
Applications of MD5
MD5's speed and simplicity have made it popular in numerous applications beyond just security. It is often used to verify the integrity of files, ensuring that they have not been altered over transmission or in storage. Software developers also use MD5 to quickly compare large volumes of data, as identical files will always produce the same hash.
The MD5 Tool on cassino.dev
For those needing to generate MD5 hashes, the MD5 hashing tool on cassino.dev offers a quick and efficient way to convert your data into an MD5 hash. This tool is particularly useful for developers and system administrators who need to validate file integrity or manage data securely.
Security Concerns with MD5
Despite its wide usage, MD5 is not advisable for applications that require robust security, such as hashing passwords. This is because MD5 is a very fast algorithm, which makes it susceptible to brute-force attacks. Hackers can attempt millions of hashes per second, making it feasible to crack an MD5 hash with enough time and computing power.
Future Topics: Secure Alternatives to MD5
In a forthcoming article, we will explore more secure alternatives to MD5 for password hashing and other security needs. Stay tuned to learn about algorithms that offer greater resistance to attacks and are recommended for handling sensitive data in the modern cybersecurity landscape.
Conclusion
While MD5 is effective for verifying data integrity and quick data comparison, it is no longer considered secure for sensitive applications like password hashing. As the digital world evolves, so does the need for more advanced cryptographic solutions that provide enhanced security against increasingly sophisticated attacks.
Other posts
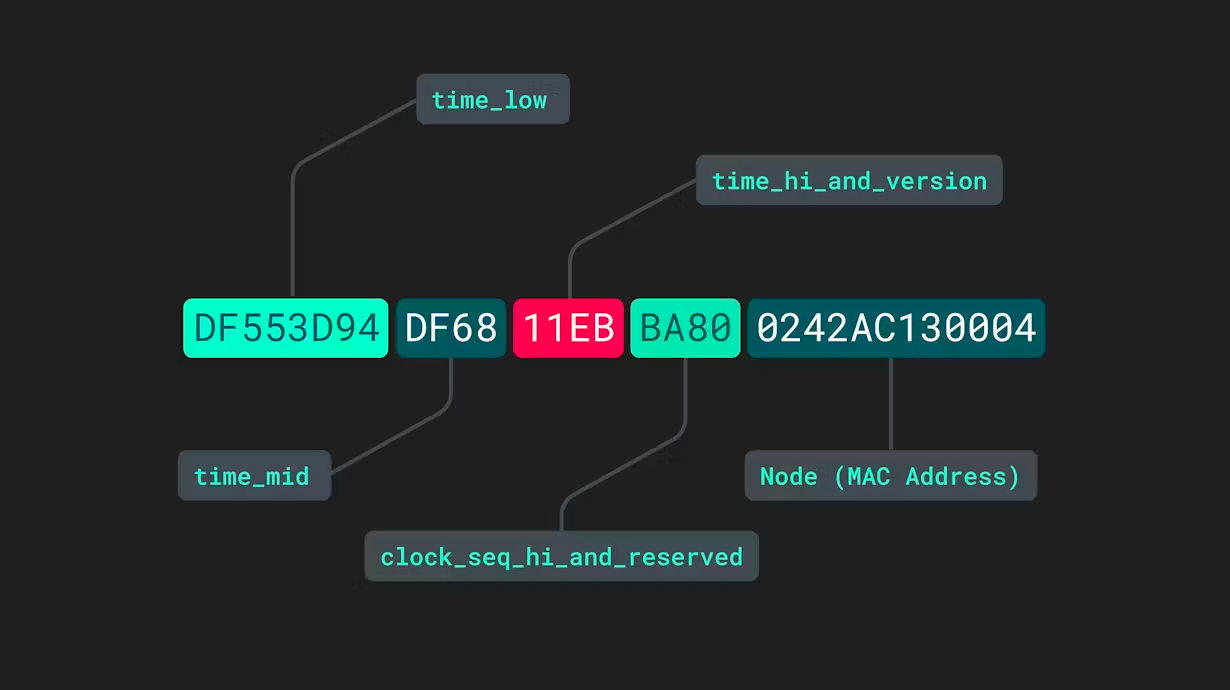
Understanding UUIDs: Types and Applications
Explore the different versions of Universally Unique Identifiers (UUIDs) and their specific uses.
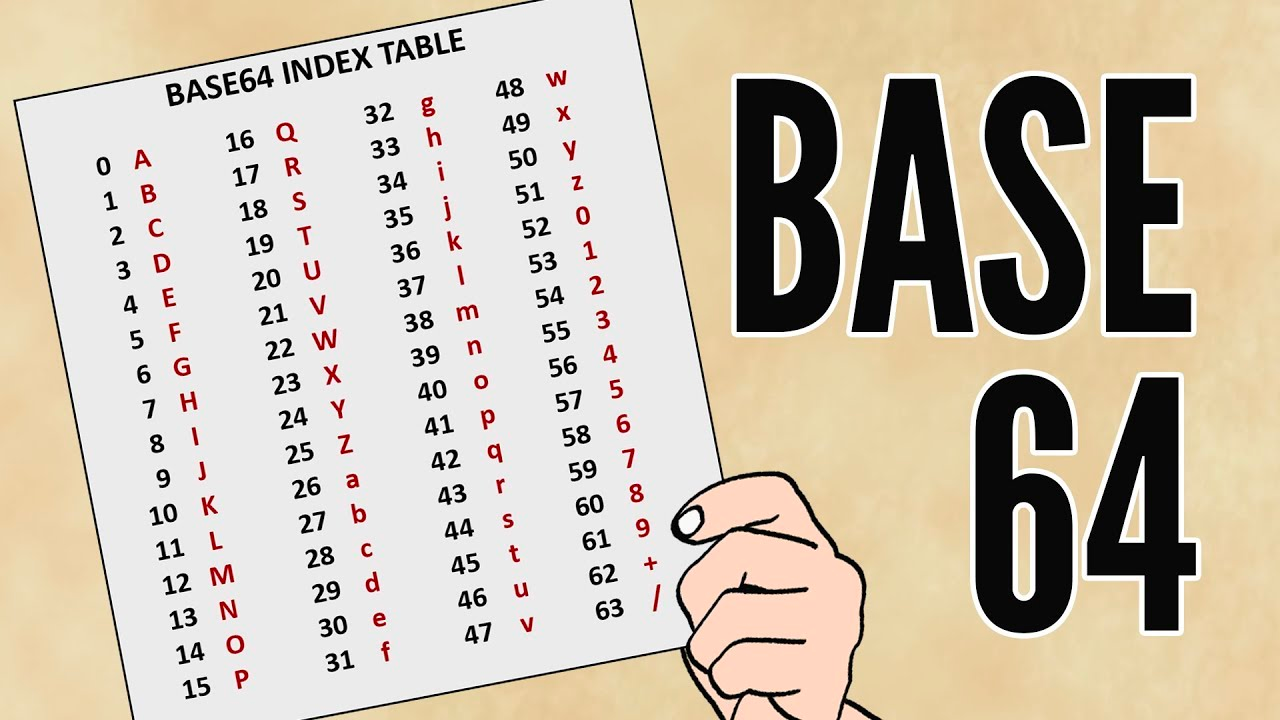
Understanding Base64: Encoding and Decoding Explained
Learn how Base64 encoding works and how it can be used to encode and decode data.

The Importance of Strong Passwords: Safeguarding Your Digital Life
Learn why strong passwords are crucial and how they protect your online accounts.
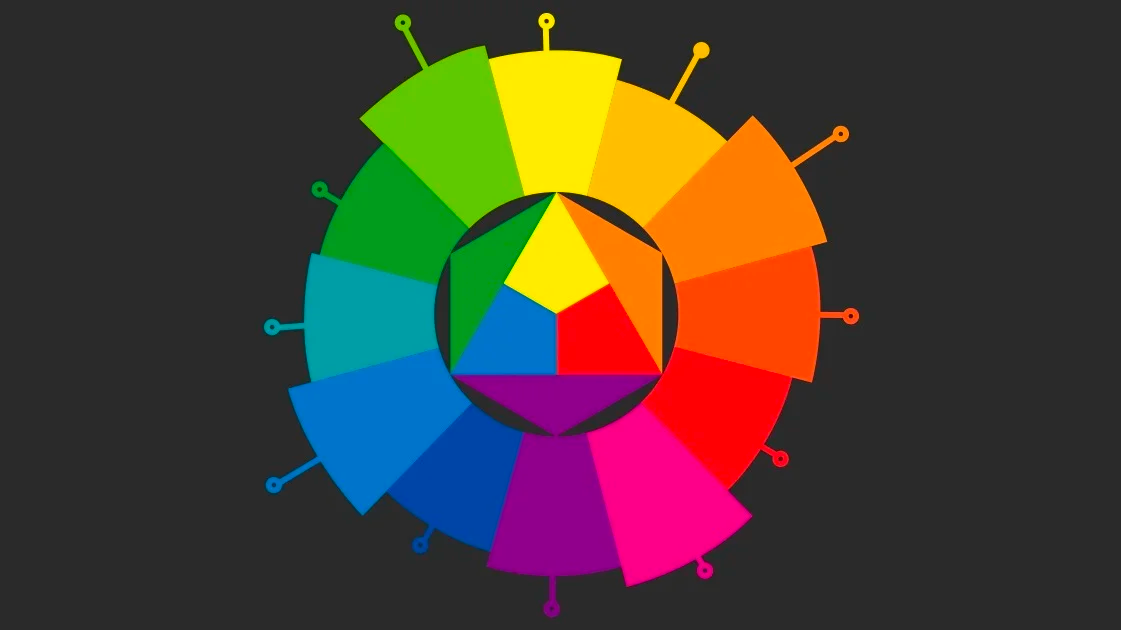
Understanding Computer Colors: RGB and Hexadecimal Explained
Dive into how computers display colors using the RGB color model and hexadecimal values.